Crypto Key Generate Rsa Modulus
- Crypto Key Generate Rsa Modulus 1024 Not Working In Packet Tracer
- Crypto Key Generate Rsa Modulus 2048
- Crypto Key Generate Rsa Modulus 1024
router(config)# hostname R1
R1(config)# ip domain-name ccie.com
–> To define a default domain name that the Cisco IOS software uses to complete unqualified host names
The label is important, I'll tell you! In a minute why C1801(config)# crypto key generate rsa modulus 1024 label C1801 The name for the keys will be: C1801% The key modulus size is 1024 bits% Generating 1024 bit RSA keys, keys will be non-exportable.OK C1801(config)#.Jan 6 15:22:25.339:%SSH-5-ENABLED: SSH 1.99 has been enabled! Switch(config)#hostname tc0001 tc0001(config)#ip domain-name jinnai73.com tc0001(config)#crypto key generate rsa The name for the keys will be: tc0001.jinnai73.com Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
R1(config)# crypto key generate rsa
–> To generate RSA key pairs
Crypto.PublicKey.RSA.generate (bits, randfunc=None, e=65537) ¶ Create a new RSA key pair. The algorithm closely follows NIST FIPS 186-4 in its sections B.3.1 and B.3.3. The modulus is the product of two non-strong probable primes. How to configure SSH on Cisco IOS. #crypto key generate rsa The name for the keys will be: R1.NETWORKLESSONS.LOCAL Choose the size of the key modulus in the range of 360 to 4096 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes. How to create a pair private/public keys using Node.js crypto? Use the crypto module from npm to generate KeyPair. Untill nodejs supports RSA key generation. Switch(config)#hostname tc0001 tc0001(config)#ip domain-name jinnai73.com tc0001(config)#crypto key generate rsa The name for the keys will be: tc0001.jinnai73.com Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
The name for the keys will be: R1.ccie.com
Choose the size of the key modulus in the range of 360 to 2048 for your General purpose keys. Choosing a key modulus
greater than 512 may take a few minutes
How many bits in the modulus [512]: 1024
–> modulus : determines the strength of the key , the higher the modulus number the strong the key is
the higher the modulus number the more CPU cycles you are going to have to use encrypt and decrypt

R1(config)# username edaoud privilege 15 secret cisco
–> To establish a username-based authentication system
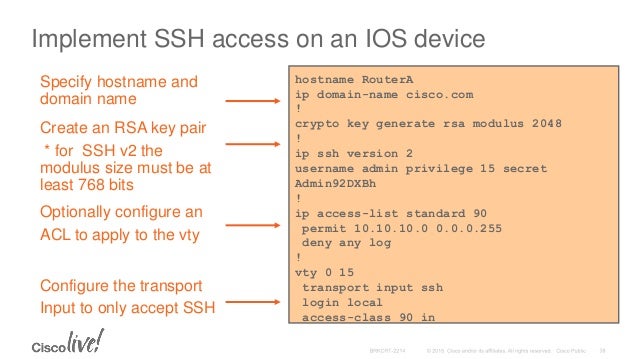
Nfs shift 2 unleashed serial key generator free download. R1(config)# line vty 0 4
–> for telnet per default, there is five lines, 0 to 4
R1(config-line)# login local
–> To enable password checking at login
R1(config-line)# transport input ssh
–> To define protocol SSH to be used to connect to a specific line of the router
R1(config)# ip ssh version 2
–> Specify protocol version to be supported
R1(config)# ip ssh time-out <0-120> ms
–> Specify SSH time-out interval
Crypto Key Generate Rsa Modulus 1024 Not Working In Packet Tracer
R1(config)# ip ssh authentication-retries <0-5>
–> Specify number of authentication retries
R1(config)# ip ssh maxstartups
–> Max concurrent session allowed
R2# ssh -l edaoud 10.1.12.1
–> Specifies the user ID to use when logging in on the remote networking device that is running the SSH server.
router# show ssh
%No SSHv2 server connections running.
%No SSHv1 server connections running.
router# sh ip ssh
SSH Disabled – version 1.99
%Please create RSA keys to enable SSH (and of atleast 768 bits for SSH v2).
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 1024 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded): NONE
Crypto Key Generate Rsa Modulus 2048
router# show control-plan host open-ports
router# show tcp
Crypto Key Generate Rsa Modulus 1024
Below Quote are taken from CCIE Routing and Switching Exam Certification Guide 4th Edition.
Using Secure Shell Protocol
Telnethas long been used to manage network devices; however, Telnet traffic is sent in clear text. Anyone
able to sniff that traffic would see your password and any other information sent during the Telnet
session. /call-of-duty-modern-warfare-3-cd-key-generator-password.html. Secure Shell (SSH) is a much more secure way to manage your routers and switches. It
is a client/server protocol that encrypts the traffic in and out through the vty ports.
Cisco routers and switches can act as SSH clients by default, but must be configured to be SSH
servers. That is, they can use SSH when connecting to another device, but require configuration
before allowing devices to connect via SSH to them. They also require some method of
authenticating the client. This can be either a local username and password, or authentication with
a AAA server (AAA is detailed in the next section).
There are two versions of SSH. SSH Version 2 is an IETF standard that is more secure than version
1. Version 1 is more vulnerable to man-in-the-middle attacks, for instance. Cisco devices support
both types of connections, but you can specify which version to use.
Telnet is enabled by default, but configuring even a basic SSH server requires several steps:
1. Ensure that your IOS supports SSH. You need a K9 image for this.
2. Configure a host name, unless this was done previously.
3. Configure a domain name, unless this was done previously.
4. Configure a client authentication method.
5. Tell the router or switch to generate the Rivest, Shamir, and Adelman (RSA) keys that will be
used to encrypt the session.
6. Specify the SSH version, if you want to use version 2.
7. Disable Telnet on the VTY lines.
8. Enable SSH on the VTY lines.
Example 18-4 shows a router being configured to act as an SSH server.
Example 18-4 SSH Configuration
router(config)# hostname R3
R3(config)# ip domain-name CCIE2B
R3(config)# username cisco password Cisco
R3(config)# crypto key generate rsa
The name for the keys will be: R3.CCIE2B
Choose the size of the key modulus in the range of 360 to 2048 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys …[OK]
R3(config)#
*May 22 02:06:51.923: %SSH-5-ENABLED: SSH 1.99 has been enabled
R3(config)# ip ssh version 2
!
R3(config)# line vty 0 4
R3(config-line)# transport input none
R3(config-line)# transport input ssh
R3(config-line)#^Z
!
R3# show ip ssh
SSH Enabled- version 2.0
Authentication timeout: 120 secs; Authentication retries: 3