Purpose Crypto Key Generate Rsa Command
- Crypto Key Generate Rsa Command Not Available
- Purpose Crypto Key Generate Rsa Command Download
- Cisco Crypto Key Generate Rsa
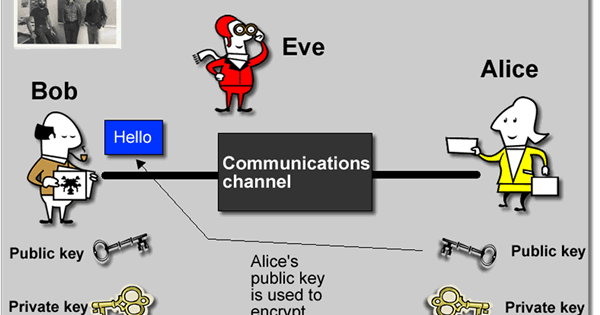
This is a fundamental part of public key cryptography. In order
Aug 03, 2007 To define the identity used by the router when participating in the Internet Key Exchange protocol, use the crypto isakmp identity global configuration command. Set an Internet Security Association Key Management Protocol identity whenever you specify preshared keys. To reset the ISAKMP identity to the default value (address). One needs to define domain-name before it's possible to generate SSH keys: sw1(config)#crypto key generate rsa% Please define a domain-name first. Sw1(config)#ip domain-name test.net sw1(config)#crypto key generate rsa The name for the keys will be: sw1.test.net Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys.
to make an encrypted connection, you need a public and private key
(a keypair). You hand out a public key to devices who want to speak
SSH to you which they can use to encrypt a message. Only your
private key can decrypt it. Event endpoint which speaks SSH needs
Shrew soft vpn download mac. to have a unique public/private keypair in order to ensure that
sites cannot decrypt each other's data.
So, before you can run SSH for the first time, you need to

Crypto Key Generate Rsa Command Not Available
generate a keypair. That is what the command does. RSA is one of
the most popuplar algorithms to generate a public-private
keypair.
Privacy Overview
Purpose Crypto Key Generate Rsa Command Download
Necessary cookies are absolutely essential for the website to function properly. This category only includes cookies that ensures basic functionalities and security features of the website. These cookies do not store any personal information.
Cisco Crypto Key Generate Rsa
Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. It is mandatory to procure user consent prior to running these cookies on your website.