Wep 128 Key Generator Passphrase
- Lost Wireless Encryption Key Generator WEP Key. WEP Key Converter. 128 bit key: Hot Wi Fi Links! Wi-Fi is short for wireless fidelity- used generically when referring of any type of 802.11 network, including 802.11b, 802.11a, and 802.11g. It is a trade term promulgated by the Wireless Ethernet Compatibility Alliance (WECA).
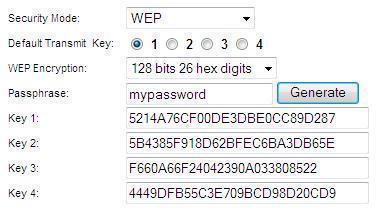
- WEP Key Generator allows you to convert a passphrase into WEP keys used by many wireless routers. It generates 40 / 60 / 104 / 128 bit WEP keys for use with.
- Highly Customisable General Password Or WEP / WPA / WPA2 Key Generator Tool This Password Generator tool has been designed to help you generate random passwords with several customisable options and character groupings.
- Wifi Password Generator - WEP Key app helps you generate secure password for your wireless network. It generates 64 bit and 128 bit secure WEP key. All you need to do is enter a simple passphrase.
Wired Equivalent Privacy (WEP) is a security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in 1997, its intention was to provide data confidentiality comparable to that of a traditional wired network.[1] WEP, recognizable by its key of 10 or 26 hexadecimal digits (40 or 104 bits), was at one time widely in use and was often the first security choice presented to users by router configuration tools.[2][3]
In 2003 the Wi-Fi Alliance announced that WEP had been superseded by Wi-Fi Protected Access (WPA). In 2004, with the ratification of the full 802.11i standard (i.e. WPA2), the IEEE declared that both WEP-40 and WEP-104 have been deprecated.[4]
Nov 02, 2004 Forum discussion: I'm looking for a wep key generator that can generate a wep key from a passphrase - the same one - everytime as long as the passphrase remains the same. I tried Ben Braly's.
WEP was the only encryption protocol available to 802.11a and 802.11b devices built before the WPA standard, which was available for 802.11g devices. However, some 802.11b devices were later provided with firmware or software updates to enable WPA, and newer devices had it built in.[5]
History[edit]
WEP was ratified as a Wi-Fi security standard in 1999. The first versions of WEP were not particularly strong, even for the time they were released, because U.S. restrictions on the export of various cryptographic technology led to manufacturers restricting their devices to only 64-bit encryption. When the restrictions were lifted, it was increased to 128-bit. Despite the introduction of 256-bit WEP, 128-bit remains one of the most common implementations.[6]
Encryption details[edit]
WEP was included as the privacy component of the original IEEE 802.11 standard ratified in 1997.[7][8] WEP uses the stream cipherRC4 for confidentiality,[9] and the CRC-32 checksum for integrity.[10] It was deprecated in 2004 and is documented in the current standard.[11]
Standard 64-bit WEP uses a 40 bit key (also known as WEP-40), which is concatenated with a 24-bit initialization vector (IV) to form the RC4 key. At the time that the original WEP standard was drafted, the U.S. Government's export restrictions on cryptographic technology limited the key size. Once the restrictions were lifted, manufacturers of access points implemented an extended 128-bit WEP protocol using a 104-bit key size (WEP-104).
A 64-bit WEP key is usually entered as a string of 10 hexadecimal (base 16) characters (0–9 and A–F). Each character represents 4 bits, 10 digits of 4 bits each gives 40 bits; adding the 24-bit IV produces the complete 64-bit WEP key (4 bits × 10 + 24 bits IV = 64 bits of WEP key). Most devices also allow the user to enter the key as 5 ASCII characters (0–9, a–z, A–Z), each of which is turned into 8 bits using the character's byte value in ASCII (8 bits × 5 + 24 bits IV = 64 bits of WEP key); however, this restricts each byte to be a printable ASCII character, which is only a small fraction of possible byte values, greatly reducing the space of possible keys.
A 128-bit WEP key is usually entered as a string of 26 hexadecimal characters. 26 digits of 4 bits each gives 104 bits; adding the 24-bit IV produces the complete 128-bit WEP key (4 bits × 26 + 24 bits IV = 128 bits of WEP key). Most devices also allow the user to enter it as 13 ASCII characters (8 bits × 13 + 24 bits IV = 128 bits of WEP key).
A 152-bit and a 256-bit WEP systems are available from some vendors. As with the other WEP variants, 24 bits of that is for the IV, leaving 128 or 232 bits for actual protection. These 128 or 232 bits are typically entered as 32 or 58 hexadecimal characters (4 bits × 32 + 24 bits IV = 152 bits of WEP key, 4 bits × 58 + 24 bits IV = 256 bits of WEP key). Most devices also allow the user to enter it as 16 or 29 ASCII characters (8 bits × 16 + 24 bits IV = 152 bits of WEP key, 8 bits × 29 + 24 bits IV = 256 bits of WEP key).
Authentication[edit]
Two methods of authentication can be used with WEP: Open System authentication and Shared Key authentication.
In Open System authentication, the WLAN client does not provide its credentials to the Access Point during authentication. Any client can authenticate with the Access Point and then attempt to associate. In effect, no authentication occurs. Subsequently, WEP keys can be used for encrypting data frames. At this point, the client must have the correct keys.
In Shared Key authentication, the WEP key is used for authentication in a four-step challenge-response handshake:
- The client sends an authentication request to the Access Point.
- The Access Point replies with a clear-text challenge.
- The client encrypts the challenge-text using the configured WEP key and sends it back in another authentication request.
- The Access Point decrypts the response. If this matches the challenge text, the Access Point sends back a positive reply.
After the authentication and association, the pre-shared WEP key is also used for encrypting the data frames using RC4.
At first glance, it might seem as though Shared Key authentication is more secure than Open System authentication, since the latter offers no real authentication. However, it is quite the reverse. It is possible to derive the keystream used for the handshake by capturing the challenge frames in Shared Key authentication.[12] Therefore, data can be more easily intercepted and decrypted with Shared Key authentication than with Open System authentication. If privacy is a primary concern, it is more advisable to use Open System authentication for WEP authentication, rather than Shared Key authentication; however, this also means that any WLAN client can connect to the AP. (Both authentication mechanisms are weak; Shared Key WEP is deprecated in favor of WPA/WPA2.)
Weak security[edit]
Because RC4 is a stream cipher, the same traffic key must never be used twice. The purpose of an IV, which is transmitted as plain text, is to prevent any repetition, but a 24-bit IV is not long enough to ensure this on a busy network. The way the IV was used also opened WEP to a related key attack. For a 24-bit IV, there is a 50% probability the same IV will repeat after 5,000 packets.
In August 2001, Scott Fluhrer, Itsik Mantin, and Adi Shamir published a cryptanalysis of WEP[13] that exploits the way the RC4 ciphers and IV are used in WEP, resulting in a passive attack that can recover the RC4 key after eavesdropping on the network. Depending on the amount of network traffic, and thus the number of packets available for inspection, a successful key recovery could take as little as one minute. If an insufficient number of packets are being sent, there are ways for an attacker to send packets on the network and thereby stimulate reply packets which can then be inspected to find the key. The attack was soon implemented, and automated tools have since been released. It is possible to perform the attack with a personal computer, off-the-shelf hardware and freely available software such as aircrack-ng to crack any WEP key in minutes.
Cam-Winget et al.[14] surveyed a variety of shortcomings in WEP. They write 'Experiments in the field show that, with proper equipment, it is practical to eavesdrop on WEP-protected networks from distances of a mile or more from the target.' They also reported two generic weaknesses:
- the use of WEP was optional, resulting in many installations never even activating it, and
- by default, WEP relies on a single shared key among users, which leads to practical problems in handling compromises, which often leads to ignoring compromises.
In 2005, a group from the U.S. Federal Bureau of Investigation gave a demonstration where they cracked a WEP-protected network in three minutes using publicly available tools.[15] Andreas Klein presented another analysis of the RC4 stream cipher. Klein showed that there are more correlations between the RC4 keystream and the key than the ones found by Fluhrer, Mantin and Shamir which can additionally be used to break WEP in WEP-like usage modes.
In 2006, Bittau, Handley, and Lackey showed[2] that the 802.11 protocol itself can be used against WEP to enable earlier attacks that were previously thought impractical. After eavesdropping a single packet, an attacker can rapidly bootstrap to be able to transmit arbitrary data. The eavesdropped packet can then be decrypted one byte at a time (by transmitting about 128 packets per byte to decrypt) to discover the local network IP addresses. Finally, if the 802.11 network is connected to the Internet, the attacker can use 802.11 fragmentation to replay eavesdropped packets while crafting a new IP header onto them. The access point can then be used to decrypt these packets and relay them on to a buddy on the Internet, allowing real-time decryption of WEP traffic within a minute of eavesdropping the first packet.
In 2007, Erik Tews, Andrei Pychkine, and Ralf-Philipp Weinmann were able to extend Klein's 2005 attack and optimize it for usage against WEP. With the new attack[16] it is possible to recover a 104-bit WEP key with probability 50% using only 40,000 captured packets. For 60,000 available data packets, the success probability is about 80% and for 85,000 data packets about 95%. Using active techniques like deauth and ARP re-injection, 40,000 packets can be captured in less than one minute under good conditions. The actual computation takes about 3 seconds and 3 MB of main memory on a Pentium-M 1.7 GHz and can additionally be optimized for devices with slower CPUs. The same attack can be used for 40-bit keys with an even higher success probability.
In 2008 the Payment Card Industry (PCI) Security Standards Council updated the Data Security Standard (DSS) to prohibit use of WEP as part of any credit-card processing after 30 June 2010, and prohibit any new system from being installed that uses WEP after 31 March 2009. The use of WEP contributed to the TJ Maxx parent company network invasion.[17]
Remedies[edit]
Use of encrypted tunneling protocols (e.g. IPSec, Secure Shell) can provide secure data transmission over an insecure network. However, replacements for WEP have been developed with the goal of restoring security to the wireless network itself.
802.11i (WPA and WPA2)[edit]
The recommended solution to WEP security problems is to switch to WPA2. WPA was an intermediate solution for hardware that could not support WPA2. Both WPA and WPA2 are much more secure than WEP.[18]Linux generate ssh key for git. To add support for WPA or WPA2, some old Wi-Fi access points might need to be replaced or have their firmware upgraded. WPA was designed as an interim software-implementable solution for WEP that could forestall immediate deployment of new hardware.[19] However, TKIP (the basis of WPA) has reached the end of its designed lifetime, has been partially broken, and had been officially deprecated with the release of the 802.11-2012 standard.[20]
Implemented non-standard fixes[edit]
WEP2[edit]
This stopgap enhancement to WEP was present in some of the early 802.11i drafts. It was implementable on some (not all) hardware not able to handle WPA or WPA2, and extended both the IV and the key values to 128 bits.[21] It was hoped to eliminate the duplicate IV deficiency as well as stop brute force key attacks.
After it became clear that the overall WEP algorithm was deficient (and not just the IV and key sizes) and would require even more fixes, both the WEP2 name and original algorithm were dropped. The two extended key lengths remained in what eventually became WPA's TKIP.
What Is A Wpa Passphrase
WEPplus[edit]
WEPplus, also known as WEP+, is a proprietary enhancement to WEP by Agere Systems (formerly a subsidiary of Lucent Technologies) that enhances WEP security by avoiding 'weak IVs'.[22] It is only completely effective when WEPplus is used at both ends of the wireless connection. As this cannot easily be enforced, it remains a serious limitation. It also does not necessarily prevent replay attacks, and is ineffective against later statistical attacks that do not rely on weak IVs.[23]
Key Generator For Games
Dynamic WEP[edit]
Dynamic WEP refers to the combination of 802.1x technology and the Extensible Authentication Protocol. Dynamic WEP changes WEP keys dynamically. It is a vendor-specific feature provided by several vendors such as 3Com.
The dynamic change idea made it into 802.11i as part of TKIP, but not for the actual WEP algorithm.
See also[edit]
References[edit]
- ^IEEE Standard for Information Technology- Telecommunications and Information Exchange Between Systems-Local and Metropolitan Area Networks-Specific Requirements-Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE STD 802.11-1997. November 1997. pp. 1–445. doi:10.1109/IEEESTD.1997.85951. ISBN1-55937-935-9.
- ^ abAndrea Bittau; Mark Handley; Joshua Lackey. 'The Final Nail in WEP's Coffin'(PDF). Retrieved 2008-03-16.Cite journal requires
journal=(help) - ^'Wireless Adoption Leaps Ahead, Advanced Encryption Gains Ground in the Post-WEP Era' (Press release). RSA Security. 2007-06-14. Archived from the original on 2008-02-02. Retrieved 2007-12-28.
- ^'What is a WEP key?'. Archived from the original on April 17, 2008. Retrieved 2008-03-11. -- See article at the Wayback Machine
- ^'SolutionBase: 802.11g vs. 802.11b'. techrepublic.com.
- ^Fitzpatrick, Jason (September 21, 2016). 'The Difference Between WEP, WPA and WAP2 Wi-Fi Passwords'. How to Geek. Retrieved November 2, 2018.
- ^Harwood, Mike (29 June 2009). 'Securing Wireless Networks'. CompTIA Network+ N10-004 Exam Prep. Pearson IT Certification. p. 287. ISBN978-0-7897-3795-3. Retrieved 9 July 2016.
WEP is an IEEE standard introduced in 1997, designed to secure 802.11 networks.
- ^Walker, Jesse. 'A History of 802.11 Security'(PDF). Rutgers WINLAB. Intel Corporation. Archived from the original(PDF) on 9 July 2016. Retrieved 9 July 2016.
IEEE Std 802.11-1997 (802.11a) defined Wired Equivalent Privacy (WEP).
- ^'WPA Part 2: Weak IV's'. informit.com. Archived from the original on 2013-05-16. Retrieved 2008-03-16.
- ^'An Inductive Chosen Plaintext Attack against WEP/WEP2'. cs.umd.edu. Retrieved 2008-03-16.
- ^IEEE 802.11i-2004: Medium Access Control (MAC) Security Enhancements(PDF). 2004. Archived from the original(PDF) on 2007-11-29. Retrieved 2007-12-18.
- ^Nikita Borisov, Ian Goldberg, David Wagner. 'Intercepting Mobile Communications: The Insecurity of 802.11'(PDF). Retrieved 2006-09-12.Cite journal requires
journal=(help)CS1 maint: multiple names: authors list (link) - ^Fluhrer, Scott; Mantin, Itsik; Shamir, Adi (2001). 'Weaknesses in the Key Scheduling Algorithm of RC4'(PDF).
- ^Cam-Winget, Nancy; Housley, Russ; Wagner, David; Walker, Jesse (May 2003). 'Security Flaws in 802.11 Data Link Procotols'(PDF). Communications of the ACM. 46 (5): 35–39.
- ^'Wireless Features'. www.smallnetbuilder.com.
- ^Tews, Erik; Weinmann, Ralf-Philipp; Pyshkin, Andrei. 'Breaking 104 bit WEP in less than 60 seconds'(PDF).
- ^Greenemeier, Larry (May 9, 2007). 'T.J. Maxx data theft likely due to wireless 'wardriving''. Information Week. Retrieved September 3, 2012.
- ^'802.11b Update: Stepping Up Your WLAN Security'. networkmagazineindia.com. Retrieved 2008-03-16.
- ^'WIRELESS NETWORK SECURITY'(PDF). Proxim Wireless. Retrieved 2008-03-16.Cite journal requires
journal=(help) - ^'802.11mb Issues List v12'(excel). 20 Jan 2009. p. CID 98.
The use of TKIP is deprecated. The TKIP algorithm is unsuitable for the purposes of this standard
- ^'WEP2, Credibility Zero'. starkrealities.com. Retrieved 2008-03-16.
- ^'Agere Systems is First to Solve Wireless LAN Wired Equivalent Privacy Security Issue; New Software Prevents Creation of Weak WEP Keys'. Business Wire. 2001-11-12. Retrieved 2008-03-16.
- ^See Aircrack-ng
External links[edit]
xv920 join:2002-08-27 San Jose, CA | 2004-Jun-19 7:57 pm generate WEP key from passphraseI'm looking for a wep key generator that can generate a wep key from a passphrase - the same one - everytime as long as the passphrase remains the same. I tried Ben Braly's generator but it changes the key everytime despite of using the same passphrase. I just bought a laptop computer with an embedded G device for which you must enter the wep key yourself, instead of entering a passphrase and let it generate one for you. I have been successfully using a wireless network with one access point and two clients for last two years now and all devices are configured with a passphrase thus the key is automatically generated. The thing is you can not see the generated key digits anywhere. They are all masked by *. Now I have to enter these digits directly. I know the passphrase. All I need is a key generator. Thanks. | |
inmuck Idiot In The East Premium Member join:2003-01-29 Raleigh, NC | 2004-Jun-20 12:16 pm said by xv920:I'm looking for a wep key generator that can generate a wep key from a passphrase - the same one - everytime as long as the passphrase remains the same.Did you tried this one »www.warewolflabs.com/por ··· skg.html | |
2004-Jun-21 1:44 am I saw it while I was searching, and tried. If you give the passphrase in the Custom WEP Key section, it only gives you back a hexadecimal representation of whatever you have just typed. For example, if you type 'abced', then it gives you '6162636465'. This is not how it works. Are you kidding? I need something that takes any-length character string as an input passphrase and then generates 13 bytes of information that you can use as a 128(104)-bit WEP key. | ||
Shootist Premium Member join:2003-02-10 Decatur, GA | 2004-Jun-21 6:14 am 2 simple facts 1. Don't use a passphrase, just make up a key, write it down, and type it in by hand. 2. There is NO embedded wireless G device, in any notebook from any manufacturer of any model. All internal wireless cards are in the MiniPCI slot and can be removed/replaced. | |
jpg366 join:2004-04-09 Humble, TX | download company portal for mac 2004-Jun-21 9:55 pm Why don't you write a small program that will xor your passphrase with a key (you pick it and embed it in your program) and clip the highest 13 bytes from the result, and display it as hex? You're after encoding, not randomness. The commercial programs do something similar but add a pseudrandom part, probably based on the system clock value. | |
| 1 edit | 2004-Jun-22 12:27 pm I don't want to change anything in existing, working equipment. There are two wireless clients and a wireless router up and running happily for two years and I don't want to ruin that. A few days ago I bought a laptop computer with a built-in wireless interface and I just wanted to use it in my existing wireless network. For that, why would you need to do anything in any existing equipment? You would configure the new laptop the same way everybody else is working, wouldn't you? I just wanted to see this new laptop can access Internet. Two wireless venders are mixed in this network and all 3 equipments let the user enter a passphrase and then generate the WEP key from it. There should be a 'standard' way to do that. I mean, to generate a WEP key from a passphrase. I would like to write such a program myself. Can you help me? | |
Foxbat121 join:2001-04-25 Herndon, VA | 2004-Jun-22 2:44 pm Some company (I believe it is InterSil) holds the license or patent for passphrase generation. Almost all the new wireless products stop offering passphrase generation capability now to avoid paying license fee. | |
Shootist Premium Member join:2003-02-10 Decatur, GA | 2004-Jun-22 3:10 pm You're right there should be a standard but there isn't. | |
efflandt 1 editjoin:2002-01-25 Elgin, IL | 2004-Jun-22 7:02 pm Some methods generate different keys from password/passphrase than others. For example a Linux utility generates same hex key as my Linksys WAP11 v2.2 for 64(40) bit keys, but for 128(104) bit keys they differ. I think that is because Linksys generates a hex key sequence that can alternately be used for 64 or 128 bit WEP. So if you have different hardware, it is best to use actual hex keys instead of password/passphrase/ascii string. But even when I generated hex key from passphrase for Linksys WET11, it only generated the first key. I had to fill in the blanks for the other 3 alternate keys. Also sometimes the numbering of the keys varies. In Linux wlan-ng labels them 0-3 and Linksys labels them 1-4, so to use the second key would be key 1 for Linux and key 2 for Linksys. | |
Rally1 join:2000-06-12 Long Beach, CA | 2004-Sep-17 5:48 pm »www.clariondeveloper.com/wepgen/ | |
sirozha join:2001-11-18 Kennesaw, GA | 2004-Sep-17 7:08 pm The WEP key you are talking about is a static key. Your access point or your other laptop doesn't generate the same new Hex key every time you connect. It is the same exact key that you initially entered. You could have entered it directly in Hex characters or as a passphrase. So, just access your router or your other laptop and copy the Hex key to your new laptop. I don't understand why you need a program that generates the same Hex key every time. If there's such a program, than it would be even easier to break your WEP key (not that it is very difficult now. It takes only about 20 min to break it). But if you use this kind of program to generate the WEP key, than one could use a dictionary attack method to guess it. | |
Shady Bimmer Premium Member join:2001-12-03 | 2004-Sep-23 8:36 am said by xv920:If you give the passphrase in the Custom WEP Key section,Actually, that is exactly 'how it works'. If you want randomness then use the random generation buttons. If you want repeatable output based on repeatable input, then you are getting exactly what you are asking for. I know it may not be easy to understand, but there is no difference in security given any function f that accepts input x and returns y (y=f(x)). If the function instead doubled the ascii value, modded 255, then displayed the hex representation you likely would never know the difference, yet it achieves the exact same thing as just returning the character itself. quote: I need something that takes any-length character stringYou got that at the link above. But, to re-iterate what someone else said - why do you want something reproducable? If this is that important the link above is indeed what you want. To be honest, though, using reproducable keys is not the best practice. Why not use a random generator to give you the correct size key then apply that key to all your devices at the same time? Then you don't need to remember the key or how it was derived. In fact it is good practice to change keys on a regular basis anyway. | |
2004-Sep-23 8:46 am said by xv920:There are two wireless clients and a wireless quote: For that, why would you need to do anything in anyIf you've had multiple devices all using the same 128-bit key for two years (never changed) then you might as well not use encryption at all (in all honesty). If someone were interested in your network they'd have broken in long ago. The simplest method (by all means) is use a random generator to create the key you want and apply it to all the devices together. Oh - did you actually *try* to use the hex output from the link above in your device that only accepts hex? Enter the known passphrase then copy the hex. If you have multiple vendors that each accepts a passphrase and they all work together then it is very possible they are doing nothing more than this page. At worst it simply won't work and will have cost you 2 minutes time. | ||
RomanySaad Premium Member join:2001-07-31 Egypt | 2004-Sep-23 10:07 am
| |
claudeo join:2000-02-23 Redmond, WA | 2004-Sep-23 7:43 pm If you are mixing brands it is most likely that the hex key that is generated from the same passphrase will be different. I have never found two to match (but then I stopped looking pretty fast after realizing it was a waste of time). Just make up a hex key and use that. For WEP 128bit, you need 13 hex values, each of which is a pair of characters from the set 0123456789ABCDEF, or exactly 26 characters. You can even make it sort of mnemonic, but don't use something like 11223344. The hex values, or some of them, might correspond to letters or numbers, or not; it does not matter. Even better, make a list of several such keys and rotate them regularly. | |
zodiackiller @dsl.lsan03.pacbell.n | 2004-Oct-2 5:32 am Thanks. I've been searching for something like this. | |
stemeyda join:2004-01-18 Oviedo, FL | 2004-Nov-2 4:18 pm This tool ROCKS!!!! This tool will take an ascii passphrase of ANY length and generate a good 10 digit hex for 40 / 64 bit and will generate a 26 digit hex for 104 / 128 bit codes. This tool may not work on every router as the algorithm is not a standard but I have tried it now on 3 different routers and it hasn't failed me yet. If you are a traveler it is an absolute necessity to have this tool! |