He Master Secret Is Used To Generate Session Keys
A session key is a single-use symmetric key used for encrypting all messages in one communication session.A closely related term is content encryption key (CEK), traffic encryption key (TEK), or multicast key which refers to any key used for encrypting messages, contrary to other uses like encrypting other keys (key encryption key (KEK) or key wrapping key).
- He Master Secret Is Used To Generate Session Keys Pdf
- The Master Secret Is Used To Generate Session Keys In Word
- He Master Secret Is Used To Generate Session Keys 2016
Session key: A session key is an encryption and decryption key that is randomly generated to ensure the security of a communications session between a user and another computer or between two. May 12, 2017 Server Random: 32-byte pseudorandom number used to generate the Master Secret. Session Identifier: Unique number to identify the session for the corresponding connection with the client. If the session ID in the client hello message is not empty, the server will find a match in the session.
-->The Transport Layer Security (TLS) Handshake Protocol is responsible for the authentication and key exchange necessary to establish or resume secure sessions. When establishing a secure session, the Handshake Protocol manages the following:
- Cipher suite negotiation
- Authentication of the server and optionally, the client
- Session key information exchange.
Cipher Suite Negotiation
The client and server make contact and choose the cipher suite that will be used throughout their message exchange.
Authentication
In TLS, a server proves its identity to the client. The client might also need to prove its identity to the server. PKI, the use of public/private key pairs, is the basis of this authentication. The exact method used for authentication is determined by the cipher suite negotiated.
Key Exchange
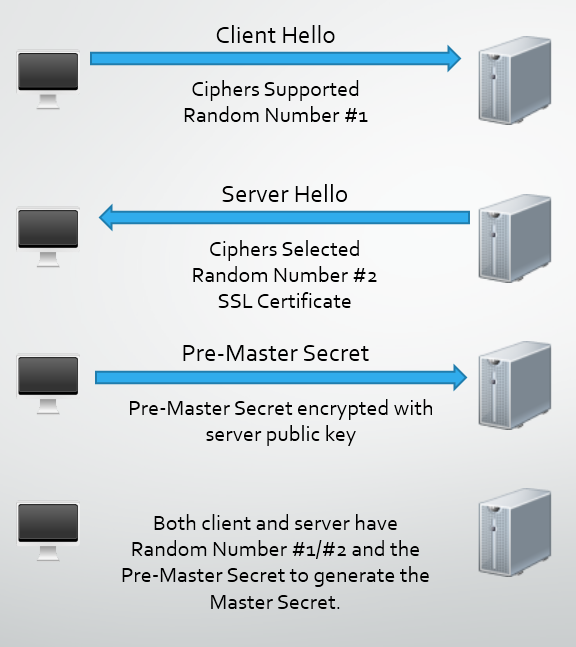
The client and server exchange random numbers and a special number called the Pre-Master Secret. These numbers are combined with additional data permitting client and server to create their shared secret, called the Master Secret. The Master Secret is used by client and server to generate the write MAC secret, which is the session key used for hashing, and the write key, which is the session key used for encryption.
Establishing a Secure Session by Using TLS
The TLS Handshake Protocol involves the following steps:
- The client sends a 'Client hello' message to the server, along with the client's random value and supported cipher suites.
- The server responds by sending a 'Server hello' message to the client, along with the server's random value.
- The server sends its certificate to the client for authentication and may request a certificate from the client. The server sends the 'Server hello done' message.
- If the server has requested a certificate from the client, the client sends it.
- The client creates a random Pre-Master Secret and encrypts it with the public key from the server's certificate, sending the encrypted Pre-Master Secret to the server.
- The server receives the Pre-Master Secret. The server and client each generate the Master Secret and session keys based on the Pre-Master Secret.
- The client sends 'Change cipher spec' notification to server to indicate that the client will start using the new session keys for hashing and encrypting messages. Client also sends 'Client finished' message.
- Server receives 'Change cipher spec' and switches its record layer security state to symmetric encryption using the session keys. Server sends 'Server finished' message to the client.
- Client and server can now exchange application data over the secured channel they have established. All messages sent from client to server and from server to client are encrypted using session key.
Resuming a Secure Session by Using TLS
The client sends a 'Client hello' message using the Session ID of the session to be resumed.
The server checks its session cache for a matching Session ID. If a match is found, and the server is able to resume the session, it sends a 'Server hello' message with the Session ID.
Note
If a session ID match is not found, the server generates a new session ID and the TLS client and server perform a full handshake.
Client and server must exchange 'Change cipher spec' messages and send 'Client finished' and 'Server finished' messages.
Client and server can now resume application data exchange over the secure channel.
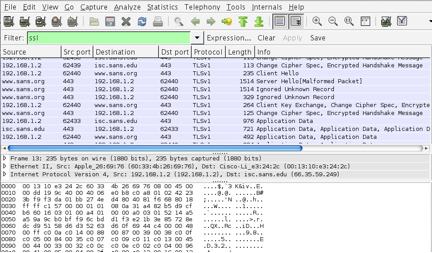
Messages Exchanged During SSL Handshake
He Master Secret Is Used To Generate Session Keys Pdf
The following steps describes the sequence of messages exchanged duringan SSL handshake. These step describe the programmatic details of the messagesexchanged during the SSL handshake.
The client sends the server the client’s SSL versionnumber, cipher settings, randomly generated data, and other information theserver needs to communicate with the client using SSL.
The server sends the client the server’s SSL versionnumber, cipher settings, randomly generated data, and other information theclient needs to communicate with the server over SSL. The server also sendsits own certificate and, if the client is requesting a server resource thatrequires client authentication, requests the client’s certificate.
The client can use some of the information sent by the serverto authenticate the server. For details, see Server Authentication During SSL Handshake. If the server cannot be authenticated,the user is warned of the problem and informed that an encrypted and authenticatedconnection cannot be established. If the server can be successfully authenticated,the client goes on to Step 4.
Using all data generated in the handshake so far, the client,with the cooperation of the server, depending on the cipher being used, createsthe pre-master secret for the session, encrypts it with the server’spublic key, obtained from the server’s certificate, sent in Step 2,and sends the encrypted pre-master secret to the server.
If the server has requested client authentication (an optionalstep in the handshake), the client also signs another piece of data that isunique to this handshake and known by both the client and server. In thiscase the client sends both the signed data and the client’s own certificateto the server along with the encrypted pre-master secret.
If the server has requested client authentication, the serverattempts to authenticate the client. For details, see Server Authentication During SSL Handshake. If the client cannot be authenticated,the session is terminated. If the client can be successfully authenticated,the server uses its private key to decrypt the pre-master secret, then performsa series of steps (which the client also performs, starting from the samepre-master secret) to generate the master secret.
Both the client and the server use the master secret to generatethe session keys/angry-birds-space-key-generator-free-download.html. , which are symmetric keys used to encryptand decrypt information exchanged during the SSL session and to verify itsintegrity—that is, to detect changes in the data between the time itwas sent and the time it is received over the SSL connection.
The client sends a message to the server informing it thatfuture messages from the client are encrypted with the session key. It thensends a separate (encrypted) message indicating that the client portion ofthe handshake is finished.
The server sends a message to the client informing it thatfuture messages from the server are encrypted with the session key. It thensends a separate (encrypted) message indicating that the server portion ofthe handshake is finished.
The SSL handshake is now complete, and the SSL session hasbegun. The client and the server use the session keys to encrypt and decryptthe data they send to each other and to validate its integrity.
Before continuing with a session, directory servers can be configuredto check that the client’s certificate is present in the user’sentry in an LDAP directory. This configuration option provides one way ofensuring that the client’s certificate has not been revoked.
The Master Secret Is Used To Generate Session Keys In Word
Both client and server authentication involve encrypting some pieceof data with one key of a public-private key pair and decrypting it with theother key:
He Master Secret Is Used To Generate Session Keys 2016
In the case of server authentication, the client encryptsthe pre-master secret with the server’s public key. Only the correspondingprivate key can correctly decrypt the secret, so the client has some assurancethat the identity associated with the public key is in fact the server withwhich the client is connected. Otherwise, the server cannot decrypt the pre-mastersecret and cannot generate the symmetric keys required for the session, andthe session is terminated.
In the case of client authentication, the client encryptssome random data with the client’s private key—that is, it createsa digital signature. The public key in the client’s certificate cancorrectly validate the digital signature only if the corresponding privatekey was used. Otherwise, the server cannot validate the digital signatureand the session is terminated.